With the NetMan Desktop Manager Access Control you can define which IP and host groups can access the system using which user accounts. Using NetMan access control is recommended, for example, if you cannot or do not wish to implement explicit login for access to the system. Even when you use anonymous user accounts, you can control which stations are permitted access, and prevent access by local user accounts in an Active Directory environment. Access control is not active when you first install NDM; no rules are defined and no user groups are configured:
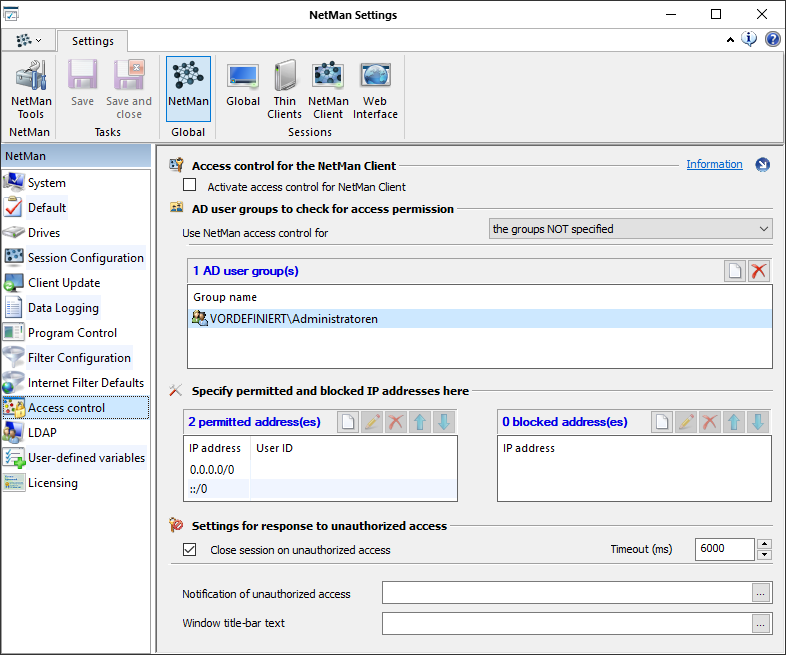
Activate access control for the NetMan Client. Activates the access control.
Use NetMan access control for. Defines the AD user groups to which the access control settings apply:
•the specified groups. Access control is applied to the specified AD user groups; other groups have unrestricted access. With this setting, a blacklist is created.
•the groups NOT specified. Access control is applied to groups that have not been specified. With this setting, a blacklist is created.
<n> AD user group(s). Enter the AD user groups in this list. Depending on your settings in NetMan Access Control, the control functions are applied to either the AD user groups listed here, or the AD user groups not listed here. Use the buttons at the top of this list to edit the list. Click the 'new' button to add a user group. Click the 'delete' button to delete the selected entry.
<n> permitted address(es). In this list, enter the IP addresses and host names that are granted access and assign user names to them.
![]() To specify IP address ranges, use CIDR notation (for example, "192.168.0.0/16" rather than "192.168.0.0.-192.168.255.255").
To specify IP address ranges, use CIDR notation (for example, "192.168.0.0/16" rather than "192.168.0.0.-192.168.255.255").
This setting is useful for anonymous users. Anonymous user names are replaced internally by the associated IP addresses replaces, which gives you better control and improved logging of access attempts by anonymous users. Use the buttons at the top of this list to edit the list. The settings are applied in the order in which they appear in this list, from top to bottom.
<n> blocked address(es). In this list, enter the IP addresses and host names that are not permitted access. Use the buttons at the top of this list to edit the list. The settings are applied in the order in which they appear in this list, from top to bottom.
Close session on unauthorized access. Closes the session when an unauthorized user attempts to access the system.
Timeout (ms). The session is closed after the period of time entered here (in milliseconds) has elapsed.
Notification of unauthorized access. You can enter a text that will be displayed when an unauthorized access attempt is made.
Window title-bar text. The text in the title bar of the message dialog.